IoT Security Explained: Protecting Your Connected Devices from Modern Threats
Are your smart devices truly secure? This guide simplifies IoT security, reveals common vulnerabilities, and offers expert tips to keep your connected world safe. Start securing your devices now!
IoT Security Explained: Protecting Your Connected Devices from Modern Threats
Table of Contents
The IoT security has changed the way we deal with technologies, by connecting the devices and making our routines easier. In smart houses or industrial systems, IoT is all over the place. On the flip side, the more reliant we are on these devices, the more we become possible victims of cybercrime. So how can we ensure the safety of our devices in the modern era? — This post will give you an in-depth IoT security overview.
Understanding IoT Security
IoT Security encompasses the strategies, technologies and procedures that are put in place to protect IoT devices and networks from being hacked. These devices include smart thermostats and industrial sensors, and more often than not, have weak security and are therefore easy targets for hackers.
Why is IoT Security Important?
-
Data Protection: Data produced by IoT devices include sensitive and personal yet sensitive. Unfortunate breaches may lead to losing identity or getting financially hacked or pledged.
-
Proper Device Functioning: Any damaged IoT device would become faulty or lose its use which would interfere with daily routines or important tasks.
-
Network Safety: Once a hacker accesses an individual device, they can take advantage of it to get into the whole system causing serious damage.
Common IoT Security Threats
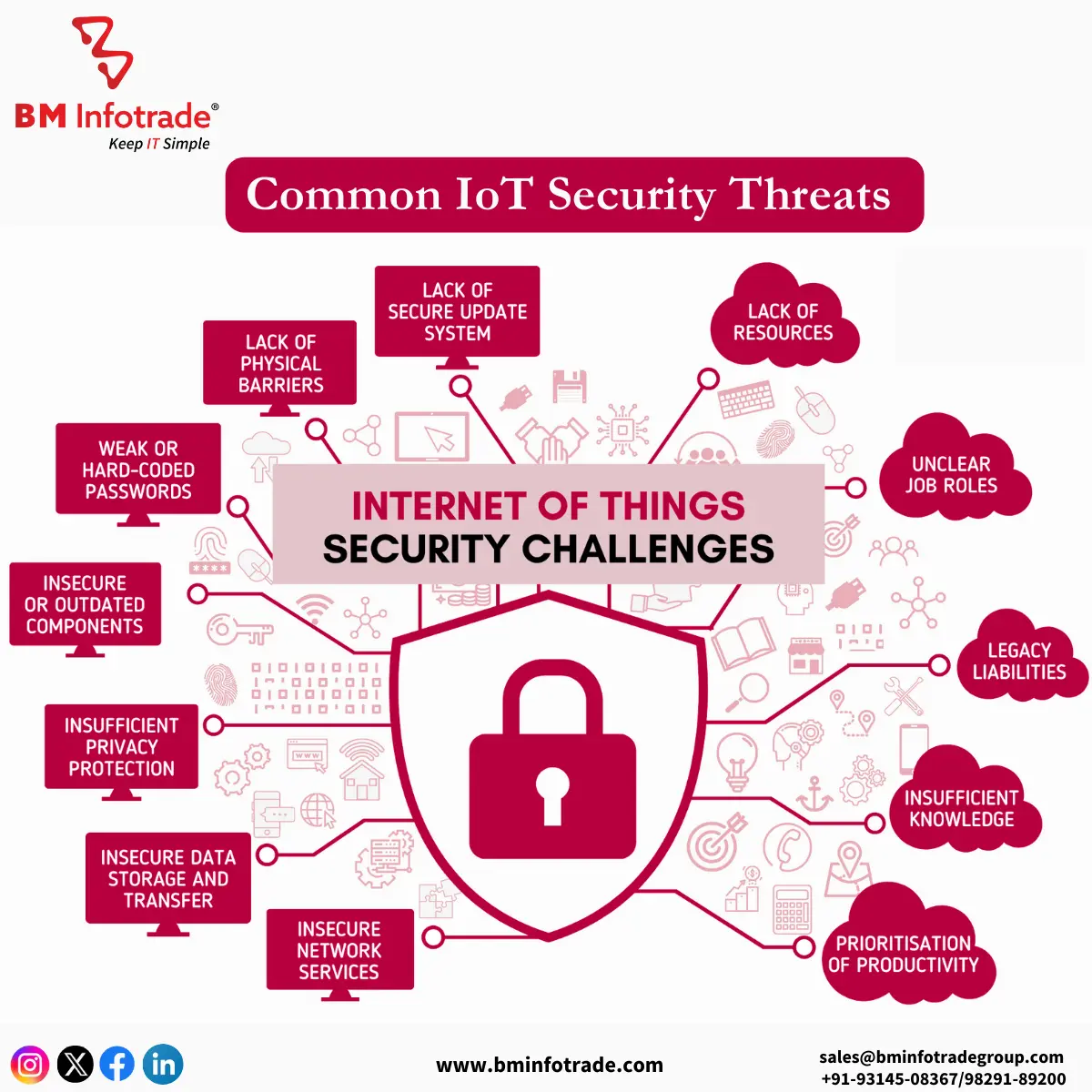
1. Managing Weak Authentication Protocols
Most users are not upbeat about changing the default usernames and passwords provided with IoT devices and that is why they tend to convert into a weak credential that hackers easily take advantage of.
2. Not Patched Vulnerabilities
Manufacturers would almost forever fork knowledge on exploits on IoT devices, especially for out of place. There would hardly, if any, timely updates provided for the devices, and they would come with outdated software.
3. Man-in-the-Middle (MitM) Attacks
A type of attack is usually carried out by hackers, intercepting and altering the data that is currently being exchanged between IoT devices and their servers.
4. DDoS (Distributed Denial of Service) Attacks.
Conversational (Phrased) IoT devices can defenselessly be hijacked, turning them into botnets and then attacks carried out, which would cause website traffic or server traffic overload.
5. Physical Tampering
Accessible areas and devices, think of cameras and sensors, going straight against IoT devices can be a very fishy thing, with many people scratching their heads at why the data can be extracted.
Key IoT Security Practices
Here is what to do to protect your IoT devices on the network:
1. Change Default Credentials
You should always replace the generic usernames and passwords with more robust and unique ones. For more difficult passwords, use a password manager.
2. Enable Two-Factor Authentication (2FA)
If possible, turn on two-factor authentication for additional security. This way, even if the hackers have the credentials, there is still a limit to what they can do.
3. Keep IoT Firmware Updated
Keep updating your IoT devices firmware to the most current version to defend them against any new threats.
4. Segment Your Network
Isolate IoT devices from other systems by putting them on their networks. This reduces the potential locations from which hackers could breach your devices.
5. Monitor Device Activity
Often review the logs of the device, for unusual operations which are, but not limited to, data transfer or several logins or more attempts than the average.
Also Read :- Top Cloud Computing Tools You Need to Know
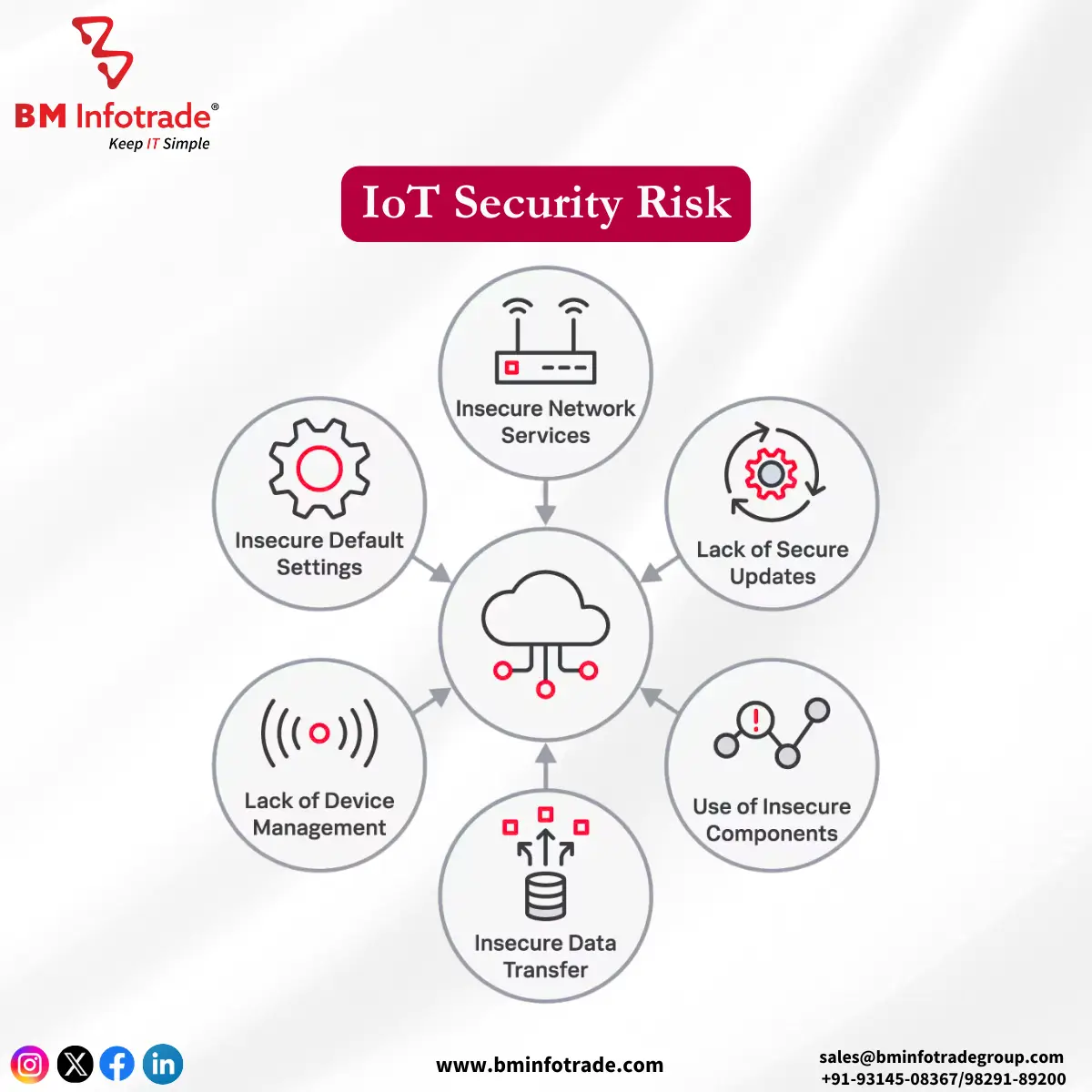
Advanced IoT Security Measures
1. Secure Gateway Utilization
IoT Gateways are intermediaries that protect devices and the cloud by placing additional layers of encryption which acts as security.
2. Adoption of End-to-End Encryption
All excessive access points of data including those transmitted by IoT are to be always encrypted to prevent any unauthorized access.
3. Artificial Intelligence-powered Threat Detection
AI and machine learning can effectively be utilized to stop unusual patterns and breaches in real-time.
4. Device Authentication
Before a device is integrated into a network, authenticate it through digital certificates.
5. Collaboration with Manufacturers
IoT devices should be bought from highly reputable manufacturers that focus on security enhancement and regular updates.
The Role of Regulations in IoT Security
Governments and regulatory bodies help in the implementation of IoT security standards. Important activities in this regard include:
-
GDPR (General Data Protection Regulation): It is concerned with data protection and privacy when implementing IoT systems.
-
NIST IoT Cybersecurity Framework: A framework of guidance for ensuring security in IoT systems.
-
IoT Cybersecurity Improvement Act: Establishes basic security requirements for IoT devices in the United States.
Compliance with these regulations enhances security and fosters confidence among consumers.
Future Trends in IoT Security
-
AI-Power Security: The threats will be identified in real-time, all thanks to Artificial Intelligence's backbone support.
-
Decentralized Interface IoT: A decentralized interface will protect the information that is exchanged among various IoT devices.
-
SSO-Multifactor: The baseline model holds the assumption of lack of trust inherently with every device therefore multilayer verification is necessary.
-
Quantum-Resistant Encryption: With the progress of quantum computers, there will be a revolution in IoT security based on possible quantum threats.
Conclusion
The Internet of Things (IoT) has certainly changed the world we live in – the convenience and efficiency it offers is unmatched as previously stated. However, this convenience comes at a price, and that price is a serious security flaw. By knowing the types of threats as well as putting in place satisfactory measures, you can defend your devices and networks from security breaches. Always be on the lookout, spend money on good technologies, and make safety in the Internet of Things the priority by routinely maintaining and updating devices.
Whether business or personal, in today’s world, protecting IoT devices should not be optional IoT devices should be IoT devices. It is possible for IoT devices to conclusively employ the security features that you can put in place.







Anshul Goyal
Group BDM at B M Infotrade | 11+ years Experience | Business Consultancy | Providing solutions in Cyber Security, Data Analytics, Cloud Computing, Digitization, Data and AI | IT Sales Leader