Boost Your Cybersecurity in 2025: A Full VAPT Guide for Modern Businesses
In today’s evolving digital world, securing your business against cyber threats is critical. This comprehensive 2025 VAPT guide covers everything you need to know about vulnerability assessment, penetration testing, and building a stronger cybersecurity posture.

Boost Your Cybersecurity in 2025: A Full VAPT Guide for Modern Businesses
Table of Contents
In cyber security, safeguarding your organization’s assets from cyber attacks is essential. VAPT or Vulnerability Assessment and Penetration Testing is a process geared towards finding and correcting security flaws in an organization’s facilities and application software. In this guide, I will cover the core aspects of VAPT, like its components, methodologies, and best practices to establish an effective cybersecurity infrastructure.
Understanding VAPT
VAPT has two features of great importance to the world of security today:
-
Vulnerability Assessment (VA): This is an audit activity that aims to systematically review and evaluate the security weaknesses of all your or your clients systems. The idea is to identify and categorize risks so that actionable mitigation strategies can be created.
-
Penetration Testing (PT): This is the same as ethical hacking, which is the simulation of an attack on a computer system to check for vulnerabilities in the system. Penetration testers exploit security flaws in a controlled environment to give a realistic picture of how a potential breach would occur, how bad it could be, and what would be the impact on business processes.
Thus, VA and PT are complementary in the sense that each fills in the intricacies which the other may be lacking when it comes to outlining security problems and solutions.
Types of VAPT
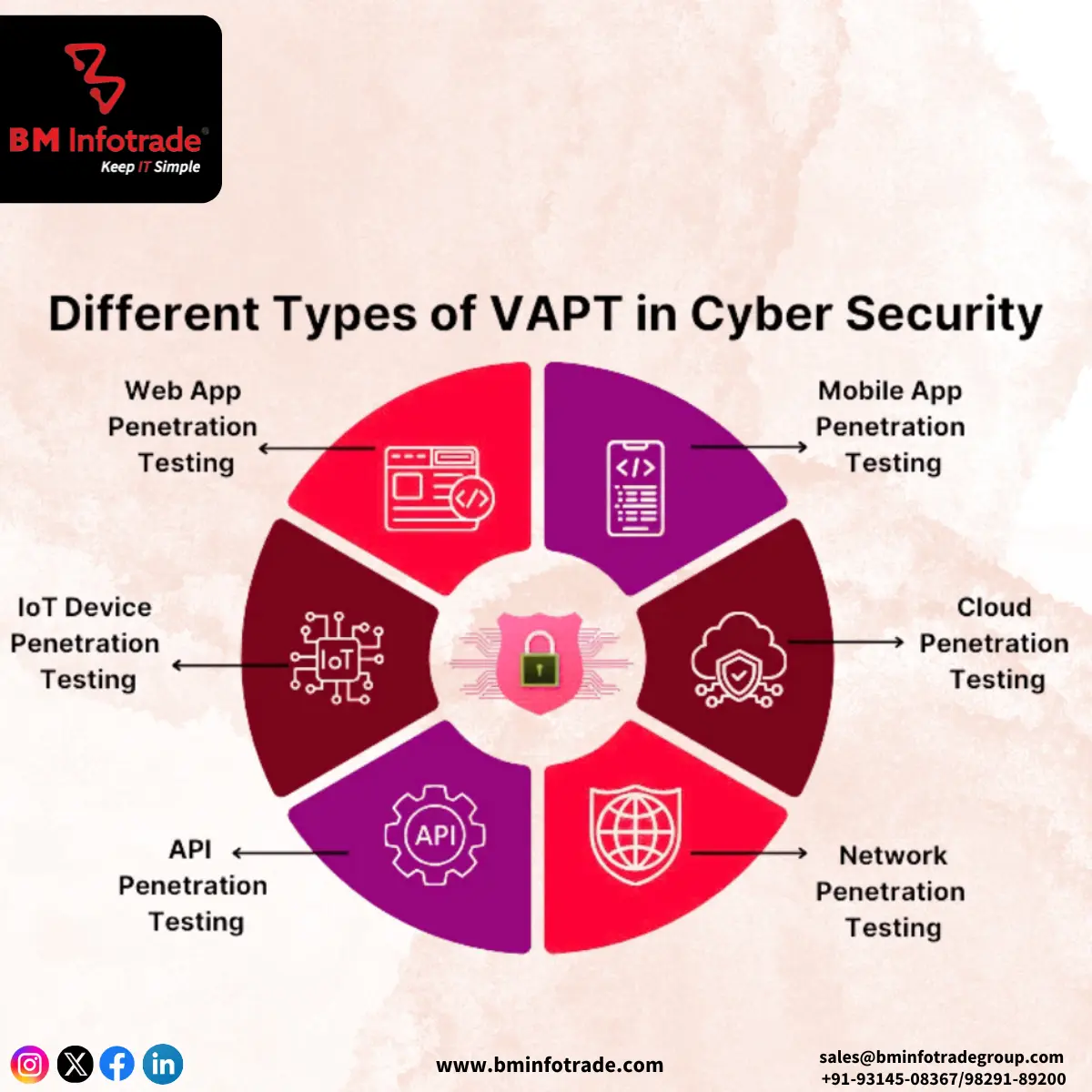
VAPT can be classified depending on the area of concentration:
-
Network VAPT: Concentrates on vulnerabilities present in a firm's network such as firewalls, routers, and switches.
-
Web Application VAPT: Involves the examination of specific weaknesses in web applications and web services APIs.
-
Mobile Application VAPT: Focus on applied security of mobile applications on iOS and Android devices.
-
Cloud VAPT: Concerns about the security of cloud-based infrastructure and services.
-
IoT VAPT: Specializes in vulnerabilities within the Internet of Things devices and their surrounding ecosystems.
Also Read:- Next-Generation Cybersecurity Trends
VAPT Methodology
The key stages in the structured VAPT methodology are:
-
Reconnaissance: Information collection of the target system.
-
Scanning: Discovery of active hosts, open ports, and services.
-
Vulnerability Assessment: Known vulnerabilities identification in the target system.
-
Penetration Testing: Attempting to take advantage of the vulnerabilities discovered.
-
Analysis and Reporting: Review results and create reports in detail.
-
Remediation and Verification: Mitigation of the verified vulnerabilities, followed by retesting.
Implementing a VAPT Program
To properly manage a VAPT program, consider the following recommendations for strong management skills.
-
Scope and Objectives Definition: Choose important assets and systems undergoing testing.
-
Test Schedule Creation: Set goals for the assessment (quarterly, bi-annual, etc.) that will be conducted regularly.
-
Testing Methodologies Selection: Choose the most appropriate testing methodologies for each asset.
-
In-house or Specialized VAPT Team Staff: Create an external or internal expert capt agonist.
-
Reporting and Remediation Processes Setting: Set protocols on how the severity of the attacks and reports are rated and where the reports should be presented.
Best Practices for Effective VAPT
Here are six recommendations that go hand-in-hand with your VAPT project, organized in a way to provides the most value:
-
Keep an Asset Inventory: Keep precise records that cover all assets.
-
Prioritize Vulnerabilities: Assess and utilize the CVSS - Common Vulnerability Scoring System Methodology Framework.
-
Conduct Both Internal and External Testing: Conduct exterior tests to mimic external attackers, and conduct internal examinations to analyze hypothetical risks posed by internal actors.
-
Embrace Automation: Use assessing and scanning automated devices for constant evaluation.
-
Stay Informed About New Vulnerabilities: Obtain nourishment from vulnerability feeds and alerts for enhanced security.
-
Conduct Red Team Exercises: Execute scenario-based testing to demonstrate actual risk occurrences that will enable advanced threats and actual attack strategies.
Also Read:- What Are DNS Zones and Records? A Complete Guide to Understanding DNS Basics
Addressing Common VAPT Challenges
Some of the issues that are likely to arise are:
-
Handling incorrect positive indications: Apply various tools to validate and corroborate the results and consider the manual confirmation of the most serious vulnerabilities.
-
Adapting to Emerging Threats: Schedule updates for your VAPT tools and methods as well as provide your security personnel with further training.
-
Assessing Complicated Setups: Prepare a detailed and well-organized plan for testing that encompasses every part of the infrastructure.
-
Managing Security with Operations: Work in close liaison with the IT and development teams to reduce interference.
Emerging Trends in VAPT
Walk on the edge by monitoring these trends:
-
AI and Machine Learning in VAPT: New tools should be available using AI for more accurate and prioritized Vulnerability detection.
-
Cloud-Native Security Testing: Use tools that are suitable for testing cloud environments.
-
DevSecOps Integration: VAPT should be part of the CI/CD pipeline for security testing at every stage of the development cycle.
Incorporating VAPT into IT Security strategy with the above-mentioned technologies, techniques, and recommendations will greatly improve the security posture of your organization allowing organization weaknesses to be identified and fixed way before they are targeted. Always remember that the threat landscape is evolving constantly, and so will the VAPT strategies.
Conclusion
Vulnerability Assessment and Penetration Testing (VAPT) is regarded as the bedrock of an effective cyber defence posture. VAPT allows organizations to proactively counter the continuously changing threats to their systems by targeting and creating real-world attacks. Put into application, an effective VAPT program puts into practice the necessary security standards and also protects sensitive information and important assets.
With cyber threats rapidly evolving and becoming a more persistent issue, being proactive instead of reactive is very important. Organizations can defend their operations, reputation, and stakeholders by putting VAPT on their schedule and embracing new trends in the security industry. Adequate investment in cybersecurity spatial capabilities should be seen today as an investment in maintaining a competitive position by creating a strong and adaptable business in the future.
How BM Infotrade Helps Businesses with VAPT
At BM Infotrade, we specialize in delivering end-to-end Vulnerability Assessment and Penetration Testing (VAPT) services tailored to modern business needs. Our expert team identifies security loopholes, tests your systems against real-world threats, and provides actionable insights to strengthen your defenses. We use industry-leading tools, manual testing techniques, and customized strategies to ensure your network, applications, and cloud environments are fully protected. Whether you're a startup or an enterprise, BM Infotrade offers scalable VAPT solutions designed to meet regulatory compliance, safeguard sensitive data, and prevent costly cyber-attacks. With BM Infotrade, businesses don't just find vulnerabilities — they fix them before attackers can exploit them, building a resilient cybersecurity framework for 2025 and beyond.







Anshul Goyal
Group BDM at B M Infotrade | 11+ years Experience | Business Consultancy | Providing solutions in Cyber Security, Data Analytics, Cloud Computing, Digitization, Data and AI | IT Sales Leader